

Encryption
Chapter 4
Encryption
How Encryption Works
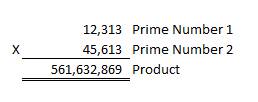
- Encryption is based on prime numbers - two prime numbers to be exact. When
multiplied together, two prime numbers will yield a product that is only
divisible by one and itself – and those two prime numbers. These prime numbers
are used in a complex algorithm to scramble (encrypt) a message or file.
Thereafter, the two prime numbers are needed again in order to unscramble
(decrypt) the message or file. An example is shown below:
Bit’s Explained
– All data stored on a computer (including prime numbers) is converted to
hexadecimal and then to binary format. A binary format is a “0” or a “1”. The
“0” or “1” is represented as a “positive” or “negative” charge on a computer’s
hard drive, or as a small of large
pit (hole) on a CD ROM. From example the letter “A” is represented on your
computer’s hard drive as “0100 0001”. Here is the complete alphabet and numbers
1 through 15 represented in binary code.
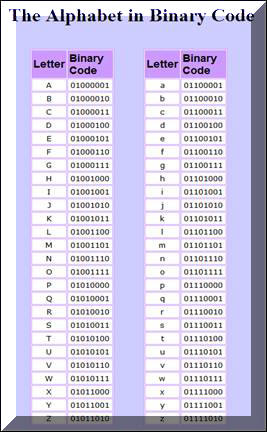

As you can see in the chart above, 8 bits of data are required to record a
single letter, or number greater than 15. Therefore if you have a 40-bit
encrypted password, you really have a 5 character password. 56 bit, 64 bit, and
128 bit encrypted passwords translate to 7, 8 and 16 character passwords. In
other words, when you use 128 bit encryption, this means that you are using
prime numbers that are 16 digits in length to generate the basis for scrambling
your data.
The Size of the Prime Numbers
- The size of the prime numbers used dictate how secure the encryption will be.
A message encrypted with 5 digit prime numbers (40-bit encryption) yields about
1.1 trillion possible results. A message encrypted with 7 digit prime numbers
(56-bit encryption) yields about 72 quadrillion possible results. However
using 128-bit encryption (16 digit numbers) yields
340,282,366,920,938,463,463,374,607,431,768,211,456 possible results.
Mathematically, It would take a super computer testing 100 billion passwords per
second, 107,829 billions years to break 128-bit encryption using brute force.
(Today’s fastest chips can handle about 256 million encryptions per second.)
Time Needed To Crack
- Mathematically speaking, based upon today’s top computing power 40-bit,
56-bit, 64-bit, and 128-bit encryption could be broken in 1 second, 19 hours, 7
months and 11,000 quadrillion years, respectively. This is why 128-bit
encryption is the standard used world-wide to protect financial transactions and
sensitive data.
|
Key Length |
1995 |
2000 |
2005 |
|
40 |
68 seconds |
8.6 seconds |
1.07 seconds |
|
56 |
7.4 weeks |
6.5 days |
19 hours |
|
64 |
36.7 years |
4.6 years |
6.9 months |
|
128 |
6.7e17 millennia |
8.4e16 millennia |
1.1e16 millennia |
|
Table of time needed to break certain key sizes using hardware
http://www.cs.bris.ac.uk/~bradley/publish/SSLP/chapter3.html
|
|||
It has been estimated that 128-bit encryption will be breakable in about 105 to
125 years (by the years 2109 to 2129).
Letters versus Numbers
- You might be interested to know that four words selected at random are much
more effective than 56 Bit encryption. According to Jeremy Bradley of the
University of Bristol, a 7-character password (56-bit) has 1,028,071,702,528
possible results. However four random words yield a total of
390,625,000,000,000,000 possible results. His basis for this claim is explained
here:
http://www.cs.bris.ac.uk/~bradley/publish/SSLP/chapter3.html.
 PGP
(Pretty Good Privacy)
PGP
(Pretty Good Privacy)
PGP or Pretty Good Privacy was released on June 5, 1991. Developed by Phil
Zimmerman, Phil first sent PGP to Allan Hoeltje and then Kelly Goen who in turn
released PGP through Internet user groups. This set off an unexpected feeding
frenzy. Volunteers around the world offered to help Phil port PGP to other
platforms, add enhancements, and generally promote the product. Fifteen months
later, in September 1992, PGP 2.0 was released for MSDOS, Unix, Commodore Amiga,
Atari, and a few other platforms, and in about ten foreign languages.
Shortly thereafter US Customs took an interest in the case. At first the
government tried to build a case against Phil for exporting weapons outside the
US, and they frequently harassed him. By doing so the government helped propel
PGP's popularity by igniting controversy that would eventually lead to the
demise of the US export restrictions on strong cryptography. Today, PGP remains
just about the only way anyone encrypts their email. And now there are a
dozen companies developing products that use the OpenPGP standard. You can
download PGP for free, or purchase a more feature rich version at this web site:
www.pgp.com.
Here is a quick introduction into using PGP:


![]()
To start using PGP, launch the product and start the wizard to generate the
encryption keys as shown below:

The PGP wizard shown above walks you through the process of creating your
encryption keys. Once you have created an encryption key, you can encrypt text,
files, folder, or e-mails using that newly created PGP encryption key. Presented
below is an example of a simple message before and after encrypting with PGP.
Original Message
![]()
Same Message as Above - Encrypted with a
PGP 128 Bit Key

It is important to point out that an encrypted message is still naked and
wide-open on the internet or on a computer hard drive – it’s just that now no
one can make sense of that message/file/e-mail without the proper decryption
key.
PGP’s Two Key System
- PGP is based on public key cryptography, a widely accepted and highly trusted
public key encryption system, by which you and other PGP users generate a key
pair consisting of a 'private key'
and a 'public key'. As its name
implies, only you have access to your private key, but in order to exchange
files with other PGP users you need a copy of their public key and they need a
copy of yours. You use your private key to sign the file attachments you send to
others and to decrypt the files they send to you. Conversely, you use the public
keys of others to send them encrypted files and to verify their digital
signatures. PGP won't route your e-mail over a Secure Socket Layer (SSL), but it
will be unreadable by anyone other than you and the person to whom it is
addressed. Keep in mind that encryption is for the message body only - it does
not hide the subject line or the headers.
SSL – A Web Based Version of PGP’s Two Key System -
One popular implementation of public-key encryption is the Secure Sockets Layer
(SSL). Originally developed by Netscape, SSL is an Internet security protocol
used by Internet browsers and Web servers to transmit sensitive information. SSL
recently became part of an overall security protocol known as Transport Layer
Security (TLS).

Look for the "s" after "http" in the address whenever you are about to enter
sensitive information, such as a credit-card number, into a form on a Web site.
In your browser, you can tell when you are using a secure protocol, such as TLS,
in a couple of different ways. You will notice that the "http" in the address
line is replaced with "https," and you should see a small padlock in the status
bar in the browser window.

The padlock symbol lets you know that you are using encryption. Basically what
this means is that a private key has been generated by the server you are
accessing, and has been sent to your computer and is being held in RAM until
needed. Once you have entered the information you want to send and press the
SUBMIT button, the key is used to encrypt the message and the data is sent to
the web server, or in the case shown above – the Delta Airlines web server.
Public-key encryption takes a lot of computing, so most systems use a
combination of public-key and symmetry. When two computers initiate a secure
session, one computer creates a symmetric key and sends it to the other computer
using public-key encryption. The two computers can then communicate using
symmetric-key encryption. Once the session is finished, each computer discards
the symmetric key used for that session. Any additional sessions require that a
new symmetric key be created, and the process is repeated.
Is Big Brother Watching You Anyway? -
When PGP was first developed, it was understood that the only person capable of
reading an e-mail encrypted with PGP was the e-mail recipient. While
unconfirmed, it is suspected that since PGP was purchased from Phil Zimmermann,
its developer, by Network Associates, Inc. (NAI) several years ago, that a
'master key' exists in the hands of both NAI and the U.S. Federal Government.
Even with this in mind, PGP is just about the safest and most reliable method of
encryption available.
In October, 2001, NAI put PGP up for sale. With no buyers, in March of 2002 NAI
dropped support and development of its PGP desktop encryption software. On
August 19, 2002, NAI sold PGP to PGP Corporation, a newly formed company. The
deal gives the new company a line of encryption products based on the PGP
algorithm, including PGPmail, PGPfile, PGPwireless, PGPkeyserver, for the
Windows and Macintosh operating systems. A full history of PGP can be found at
www.pgp.com/company/pgphistory.html


Though a freeware version of PGP does exist, the End User License Agreement
(EULA) is rather restrictive limiting it to home-based non-profit use. Freeware
PGP set-up only takes a few minutes, but users should note these facts about the
free version of PGP:
·
Does not include automatic encryption of email file attachments
·
Does not provide plug-in integration with Outlook, Outlook Express, and other
email applications
·
Does not operate with PGP Admin or other PGP deployment tools
Self Decrypting Files
1
2
Some implementations of encryption are self-decrypting – which means that the
unlocking key needed is already embedded in the file – all you need is the
password to activate the unlocking key. Consider the following two examples:





Your Friend only needs to know the password in order to
unlock the file as the unlocking key is already embedded.
Your Friend

![]()
![]()
A thief who intercepts the e-mail will have no way of
opening the e-mail, even if they know or guess the correct
password because they have no unlocking key.
A thief who intercepts the e-mail needs to only guess the
correct password to open the file – as unlocking key is
embedded.
A Thief

E-Mail Encryption Software
![]()
PKWARE’s SecureZip (www.pkware.com)
($30) – It does automatically encrypt e-mail, as well as Office files.
Save and send files securely directly from Microsoft Office® applications,
including Word®, Excel®, and PowerPoint® Secure and compress emails and
attachments in Microsoft Outlook®. Encrypt data using passphrases, X.509 digital
certificates, or both.
Google Message Encryption, (formerly Postini)
(www.google.com)
- Hosted solution that automatically encrypts email based on your policy
definitions, helping your organization avoid the financial penalties and brand
equity damage that can result from sending proprietary or regulated data via
unprotected email. Send encrypted messages to business partners and customers.
No additional software, hardware or technical training required. Automated or
user-initiated encryption for confidential emails to any recipient. Centralized
reporting of encrypted messages and policy enforcement. Centrally-managed
content inspection, encryption policies to help comply with GLBA, HIPAA, PCI DSS
and Data privacy regulations.
Entrust
Email Encryption (www.entrust.com)
- Protects private, sensitive and valuable information communicated via email.
Email encryption can be deployed using email encrypting software, secure email
servers or secure webmail centers. Entrust email encryption solutions work with
a broad range of email applications including Microsoft® Outlook/Exchange and
Lotus® Notes/Domino. It can be used by mobile users including those with RIM
BlackBerry® handheld devices and via secure web mail. Entrust email encryption
software uses S/MIME, PGP and Entrust encryption formats. Benefits: Transparent,
easy-to-use email security; Automatic encryption and digital signatures;
Integration with content analysis tools for email compliance; 'Government
strength' security validated against NIST standards.
![]()
ShyFile
($59) -
Make up a 32 character key entry, Enter the text you wish to encode, Attach
secure ShyFile to your email, Recipient simply uses a browser to decode. The
unlocking key is embedded in the file. ShyFile encodes your text (txt-
and html-files) and packs it into an extra file that is to be attached to an
outgoing email or uploaded to a website. The recipient thereof does not need to
have ShyFile installed to be able to decode since any Internet browser will open
it and prompt the user to enter the matching key phrase before decoding it.
ShyFile also encrypts binary files, which require a free demo version of ShyFile
to decode though. Simple 1on1 symmetric key entries are used, no Public and
Private Keys. ShyFile exclusively uses its own independently developed TL6144D
algorithm, offering a depth of encryption of up to 6144bit. That reaches or even
tops military requirements. A File Shredder is included to thoroughly delete a
file on your hard drive in a way no un-delete tool could ever restore it again.
ShyFile works independently from all your web based email accounts and desktop
email applications.

AnchorMail
(www.anchormail.com)
Secure email solution provides a service-based approach for encrypting ad hoc
emails and securely delivering the messages to any inbox, AnchorMail enables any
enterprise to enforce message policies and/or client-initiated trusted
e-communications that can be securely delivered to any recipient, without
requiring the receiving party to download or install any software. The
AnchorMail service is responsible for the data management, key management, user
enrollment, online opening, and secure reply, in addition to related
administrative functions (operations, backup, availability, etc.). This removes
the deployment integration and lifecycle management of a typical secure email
offering, and thus decreases the costs of resources, time, and administration.
Secure Hive (www.securehive.com) ($86) - Secure Hive is a tool for secure archiving and sharing of files. It enables you to create encrypted archives and self-extracting .exe files for secure storage and file sharing. It also includes a means of encrypting parts of, or entire, documents, email messages, etc. Secure Hive offers the enterprise a method of: Securing sensitive documents; protecting information during transfer; Securing emails.
![]()
CenturionMail (www.centurionsoft.com) ($59) - Windows based utility to send encrypted information by email. Recipients of encrypted messages receive an attachment to the email which when executed requires the user to enter a password to open it. CenturionMail is integrated in MS Outlook. One button operation within the Outlook composing window is all that is needed to send an encrypted email. Users of other email programs can still use the program through the CenturionMail interface which calls to the default email program. Supports all version of MS Outlook including Outlook 2003. Encrypted files can be sent as ZIP, CAB, or our new custom defined extension. AES: Now offering stronger 256 bit, open source encryption. Password Manager: Securely store and manage all the passwords to be used for various recipients. When using the Microsoft Outlook plug-in, it will pre-fill the default password for any recipient in the Password Manager. Password hints can also be saved and automatically sent. Shredder: Securely delete files and folders either during the encryption process (deletes the non-encrypted originals) or separately. On-the-Fly Encryption: Automatically encrypt a local copy of the files or folders being sent.
GnuPG www.gnupg.org
(Free) -
Free Software Foundation, Inc. offers GnuPG, (GNU Privacy Guard) a complete and
free replacement for PGP. Because it does not use the patented IDEA algorithm,
it can be used without any restrictions. GnuPG is a RFC2440 (OpenPGP) compliant
application. GnuPG itself is a command line tool without any graphical stuff. It
is the real crypto engine which can be used directly from a command prompt, from
shell scripts or by other programs. Therefore it can be considered as a backend
for other applications.
Conclusions
1.
You should assume that every e-mail you send has been read by more than 1,000
people. This is because all unencrypted e-mails are naked and wide open to the
world. A simpler Sniffer tool can capture your packets and reassemble your
e-mails.
2.
PGP was the first computer based encryption tool, although the existence of
coded messages (or cryptography) has been verified as far back as the Roman
Empire.
3.
Encryption works on primed numbers. According to Bill Gates in his book “The
Road Ahead”, there are more prime numbers of adequate size and length than there
are Atoms in the universe.
4.
Data on your computer is stored in binary code called “bits, which means zero’s
and one’s. These Since it takes 8 bits to represent a number or letter, it takes
40 bits to represent 5 numbers or letters, or 128 bits to represent 16 numbers
or letters. Hence when you work with 128 bit encryption this means that you are
actually working with 16 digit prime numbers.
5.
Using today’s technology, it would take about 11,000 quadrillion years to break
a 128 bit encrypted message.
6.
To protect your e-mails with encryption, you and your e-mail pal could install
PGP.
7.
Upon installing PGP, you would need to generate a set of encryption keys, and
send your locking key (private key) to your pal. You pal would do likewise
sending their locking key to you. Thereafter, all e-mails sent to one another
(including attachments) would be absolutely encrypted with 128 bit encryption.
8.
It is widely rumored that the US government secretly holds a universal code for
unlocking all PGP keys. At least this makes for a good conspiracy theory.
